Netcraft tool flags websites affected by Heartbleed
- 18 April, 2014 06:33
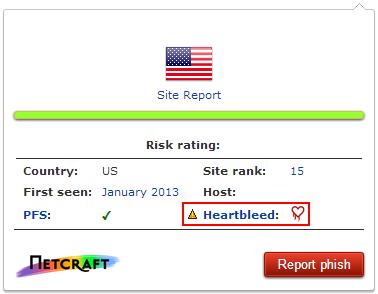
The Netcraft plug-in can warn of Heartbleed holes
Worried about how the Heartbleed vulnerability may affect your personal accounts? A new tool may be of help.
British Internet security services provider Netcraft has released a browser extension that alerts users when a site they visit hasn't been patched to protect against malicious use of the Heartbleed vulnerability, found in certain versions of the OpenSSL (Secure Socket Layer) encryption library.
The free extension can be installed on the Chrome, Firefox and Opera browsers.
Netcraft has estimated that about 17 percent of all trusted SSL (Secure Socket Layer) Web servers are vulnerable to attack due to the Heartbleed vulnerability.
OpenSSL is an open-source implementation of the SSL and TLS (Transport Layer Security) protocols, which are used to encrypt sensitive data, such as passwords, so they can transmitted securely across a public network.
Only certain versions of OpenSSL are affected by Heartbleed. These affected versions were mostly deployed in conjunction with the open source Apache and Nginx servers -- which run about 66 percent of all servers on the Internet.
A fix is available but there is no way for consumers to tell if the sites they visit have applied the patch.
Even when a site has fixed the vulnerability, attackers might have already used Heartbleed to purloin the private key of the site, which means they could steal data by way of a man-in-the-middle attack.
Netcraft's extension, an update of a previously released security tool, checks to see if the site could be vulnerable to the Heartbleed bug, using data from a prior Internet-wide automated survey the company conducted.
If so, the software then checks the private key certificate of the site a user is visiting to see if it has been updated since the Heartbleed disclosure. If not, the site is flagged as unsafe.
Joab Jackson covers enterprise software and general technology breaking news for The IDG News Service. Follow Joab on Twitter at @Joab_Jackson. Joab's e-mail address is Joab_Jackson@idg.com

