Malware scam zeroes in on ANZ customers
- 11 July, 2017 12:38

ANZ bank customers' inboxes are being hit by a fake email loaded with malware seeking to steal recipients' data.
Email filtering company MailGuard has revealed that a “highly convincing” fake ANZ bank invoice started circulating at 9:05AM on 11 July.
In an effort to convince victims of its legitimacy, the crims behind the exploit have included a legitimate security note to the fake emails that reads: “ANZ will not send you an email or SMS asking you to verify account details, financial details or login details for ANZ Phone Banking, ANZ Internet Banking or ANZ Mobile Banking”.
There are two key things that separate the fake email from legitimate ones, according to MailGuard.
“ANZ bank, following industry best-practice, tells its customers their statement is available and to log on to ANZ Internet Banking to view it,” MailGuard CEO, Craig McDonald, said in a statement.
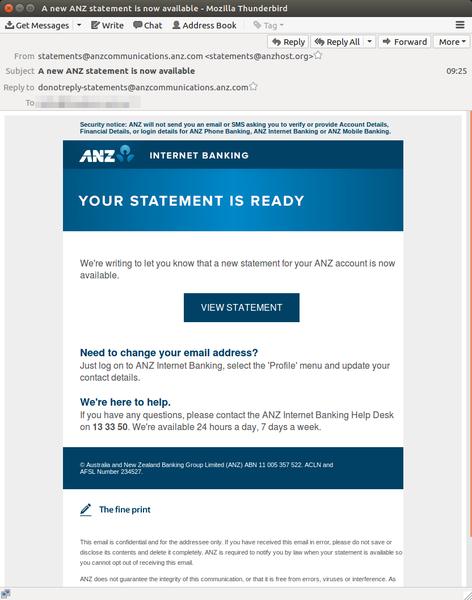
“But the scam version has a ‘View statement’ button. This button launches the download of malware onto a victim’s system. It takes the form of a .ZIP archive file containing a malicious JavaScript file,” he said.
The exact type of malware isn’t yet clear, according to MailGuard, but it is designed to steal private information from local internet browsers, install itself for auto-run at Windows startup and implement a process that significantly delays the analysis task.
The cybercriminals are using a domain registered in China just days ago.
However, the fake email uses ANZ's real display name statements @ anzcommunications.anz. com [altered], which is the real domain used by ANZ to issue legitimate invoice statement notices.
But by hovering over the address, recipients are able to see that the real, if dodgy address behind the attack is in fact: statements @ anzhost. org [altered].
The fresh malware campaign comes just a day after MailGuard identified fake ASIC emails loaded with malware, calling the exploit one of the “largest-scale” malware deliveries identified by the company in the past 12 months. The attack began just after the start of the working day on 10 July and quickly escalated.

